Wi-Fi is an abridgement for Wireless Fidelity, a networking technology that connects computers and other network devices using radio waves. Wireless Access Points (WAP), or Access Points (AP), allow wireless devices to connect to both wireless and wired networks. Having a Cisco wireless network makes it easier to bring new devices online, and it also provides flexible support to mobile end users.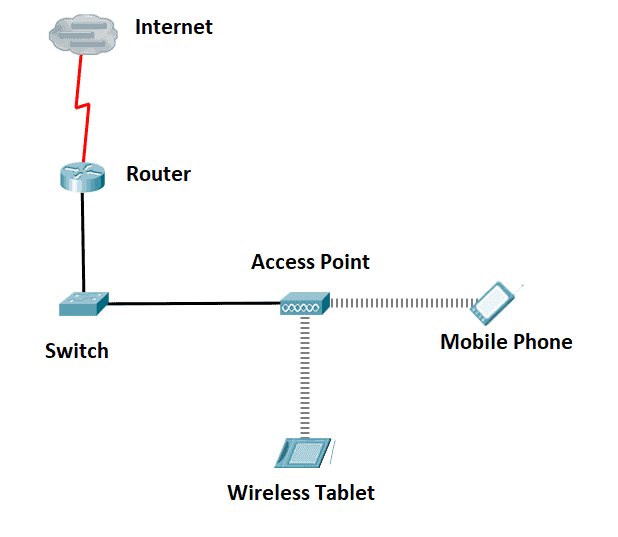
Unlike in wired networks, where data is transmitted through fiber and copper cables, the Wi-Fi network transmits data across the air in accordance with the transmitter’s antenna pattern, and it could reach any Wi-Fi-enabled devices that are within the range.
In our figure below, let’s consider that User1 is trying to send confidential data to User2. But because a Malicious User is within the wireless range of the wireless access point, it could potentially gain access to the same confidential data. The convenience of Wi-Fi networks also makes it easy for transmissions to be overheard and exploited by malicious users. Therefore, we need to implement Wi-Fi security.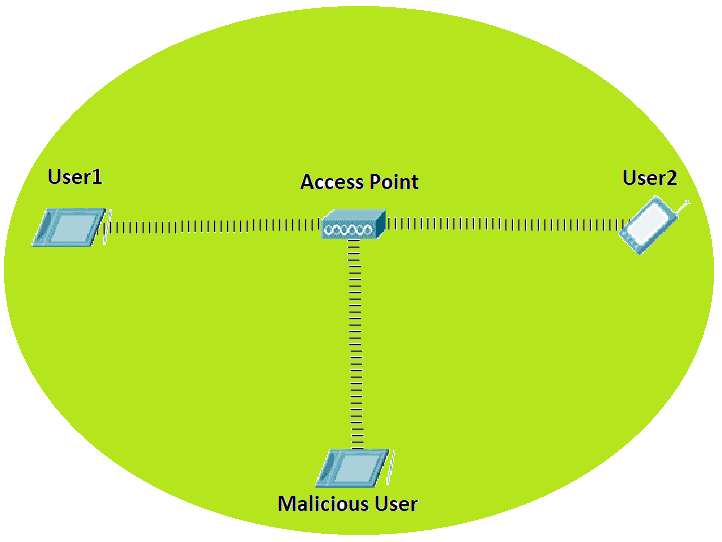
Common Wireless Security Protocols
Listed below are the most common WiFi security protocols or standards implemented for our wireless network security:
1. 1999: Wired Equivalent Privacy (WEP) – is a security option that uses the RC4 cipher algorithm to encrypt every frame so that eavesdroppers can’t read the contents.
WEP supports two WiFi security authentication modes:
- Open Authentication – The wireless client doesn’t provide any credentials and only uses WEP encryption to encrypt data frames.
- Shared Key Authentication – WEP key is used for both authentication and encryption.
The IEEE declared in 2004 that WEP had been deprecated as it failed to meet its security goals.
2. 2003: Wi-Fi Protected Access (WPA) – this wireless security standard uses Temporal Key Integrity Protocol (TKIP), which recycled some items from WEP, and it still uses the RC4 algorithm. TKIP uses 256-bit keys instead of the 64 and 128-bit keys in WEP.
3. 2004: WPA2 – the most significant upgrade in WPA2 is that it uses AES-CCMP encryption instead of the old RC4 encryption. For backward compatibility reasons, you can still use TKIP as a fallback mechanism for WPA clients. It also introduced Wi-Fi Protected Setup (WPS). If you want to connect to a network that uses a pre-shared key, then you need to know the SSID and the pre-shared key.
4. 2018: WPA3 – still uses AES but replaced CCMP with the Galois/Counter Mode Protocol (GCMP). The key length for AES has increased.
Another new feature of WPA3 is Simultaneous Authentication of Equals or SAE. Instead of a four-way handshake authentication, SAE improves the security of the initial key exchange and offers better protection against offline dictionary-based attacks.
WPA3 Uses Either of These Two WiFi Security Modes:
- WPA3-Personal mode – offers 128-bit encryption, and it uses WPA-PSK/pre-shared key.
- WPA3–Enterprise – offers 192-bit encryption, and it uses AAA/RADIUS authentication server.
As more and more network vulnerabilities are being discovered, we should always plan our security measures and get one step ahead of the attackers. We can avoid unsecured wireless networks by always selecting the highest WPA version whenever possible.
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
