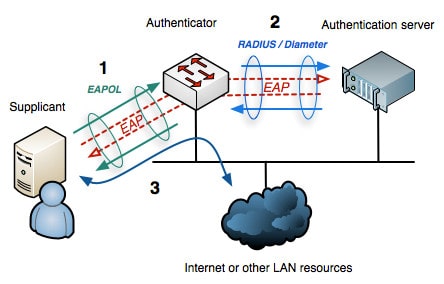
IEEE 802.1x is a standard defined by the IEEE 802.1x working group for addressing port-based access control employing authentication for wired and wireless networks. There are three main components that we have to take into account, namely the Supplicant, Authenticator, and the Authentication Server (AS).
The Supplicant is the user or client allowed to access the network. While the Authenticator is any network device such as a Wireless Access Point or an Ethernet Switch, and the Authentication Server (AS) is a trusted server that does the authentication mechanism of the network access by receiving, processing, and responding to various requests from the clients and also the one who decides and tells the authenticator to either allow or deny the access and apply various settings to the user.
NOTE:
Authentication servers usually run software supporting the RADIUS and Extensible Authentication Protocol (EAP). In some cases, the AS software may be running on the authenticator hardware, such as the RADIUS server.
Common EAP Based Authentication Methods
Below is an overview of the commonly used EAP methods:
Light Weight EAP (LEAP) – the authentication process is where the client simply provides the AS its credentials, such as the username and password. Encrypted challenge messages are exchanged between the AS and client to ensure that the client is authorized to access the network.
EAP Flexible Authentication by Secure Tunneling (EAP-FAST) – there are three phases to gain access using this EAP method wherein a Protected Access Credential (PAC) should be passed between the AS and the supplicant.
Protected EAP (PEAP) – uses inner and outer authentication. Nevertheless, the AS presents a digital certificate to authenticate itself with the supplicant in the outer authentication.
EAP Transport Layer Security (EAP-TLS) – the AS and the supplicant exchange certificates and can authenticate each other. A TLS tunnel is built afterward to exchange encryption key material securely. EAP-TLS is considered the most secure wireless authentication method available; however, implementing it can sometimes be complex.
NOTE:
EAP-TLS is practical only if wireless clients can receive and utilize digital certificates. Many wireless devices, such as communicators, medical devices, and RFID tags, have an underlying operating system that can’t interface with a CA or use certificates.
IEEE 802.1x Authentication Process
The authentication method begins when the client device requests to connect to the network. The authenticator receives the request and creates a virtual port with the supplicant. The authenticator acts as a proxy for the end user, passing authentication information to and from the authentication server on its behalf. The authenticator limits traffic to authentication data to the server. A negotiation takes place, which includes:
- The client may send an EAP-start message.
- The access point sends an EAP-request identity message.
- The client’s EAP-response packet with the client’s identity is “proxied” to the authentication server by the authenticator.
- The authentication server challenges the client to prove itself and may send its credentials to prove itself to the client (if using mutual authentication).
- The client checks the server’s credentials (if using mutual authentication) and then sends its credentials to the server to prove itself.
- The authentication server accepts or rejects the client’s request for connection.
- If the end user is accepted, the authenticator changes the virtual port with the end user to an authorized state allowing full network access to that end user.
- The client’s virtual port is changed back to the unauthorized state at log-off.
Identity-Based Networking Services (IBNS)
IBNS is distinct from IEEE 802.1x but has the same 802.1x functionality. IBNS is a systems security framework that delivers network authentication methods, and a part of it uses IEEE 802.1x.
IEEE 802.1x is a standard defined by IEEE 802.1x working group for addressing port-based access control using authentication. It defines a standard link-layer protocol that is used for transporting higher-level authentication protocols, and the actual enforcement is via MAC-based filtering and port state monitoring.
Benefits of Identity-Based Networking
There are quite a number of advantages to using identity-based networking, such as:
- Offers complete visibility, access control, and audit of all interactions based on user identity, machine identity, and health status
- Secures remote access
- Enables quick resolution of network incidents
- Prevents unauthorized access to network resources
- Controls assets, applications, and data
- Ensures maximum service availability
- Increases user productivity gains
- Reduces operating costs
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training: