The Cisco port security violation mode is a port security feature that restricts input to an interface when it receives a frame that breaks the port security settings on the said interface. This security mechanism is used in Cisco Catalyst switches to secure their ethernet ports from unauthorized users by limiting and identifying MAC addresses of the peripheral that are allowed to access the port.
Enabling the port security violation feature on the switch ports means that each port can be configured to take advantage of one of the three violation modes that define the necessary actions to take when a violation happens. These modes cause the switch to discard the violating frame (the frame whose source MAC address would drive the number of learned MAC addresses over the limit).
Configuring Port Security on a Switch Port
To limit or discard an unwanted frame on a switch interface, we need to limit and identify the MAC address of the peripherals that are allowed to access the port. We need to configure port security to these interfaces.
Step 1: Enter interface configuration mode and input the physical interface to configure. We will be using gigabitEthernet 2/1 as an example.
Switch(config)# interface gigabitEthernet 2/1
Step 2: Set the interface mode to access. The default mode, which is dynamic desirable, cannot be configured to be a secured port.
Switch(config-if)# switchport mode access
Step 3: Enable port security on the interface.
Switch(config-if)# switchport port-security
Step 4: Set the maximum number of secure MAC addresses for the interface, which ranges from 1 to 3072, wherein the default value is 1.
Switch(config-if)# switchport port-security maximum {1-3072}
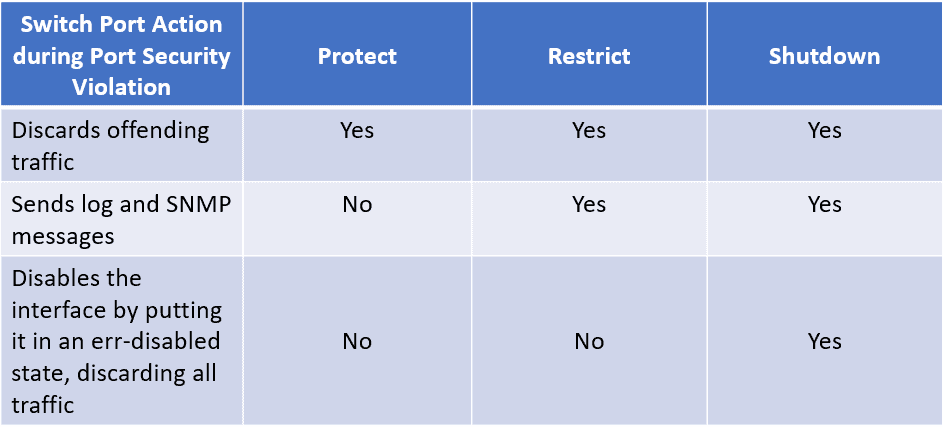
Step 5: Configure the violation mode on the port. Actions that shall be taken when a security violation is detected. Refer to the table below for the actions to be taken.
Switch(config-if)# switchport port-security violation {protect| restrict | shutdown}
When a secure port is in an error-disabled state, you can bring it out of the state by issuing the command ‘errdisable recovery cause psecure-violation’ at the global configuration mode, or you can manually reenable it by entering the ‘shutdown’ and ‘no shutdown’ commands.
Step 6: Set the rate limit for bad packets.
Switch(config-if)# switchport port-security limit rate invalid-source-mac
Step 7: Input the identified secure MAC addresses for the interface. You can use this command to limit the maximum number of secure MAC addresses. If in case, you configure fewer secure MAC addresses than the maximum, then the remaining MAC addresses are dynamically learned.
Switch(config-if)# switchport port-security mac-address {mac_address}
Step 8: Verify your configuration by the following commands below.
Switch# show port-security address interface gigabitEthernet 2/1 Switch# show port-security address
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training: