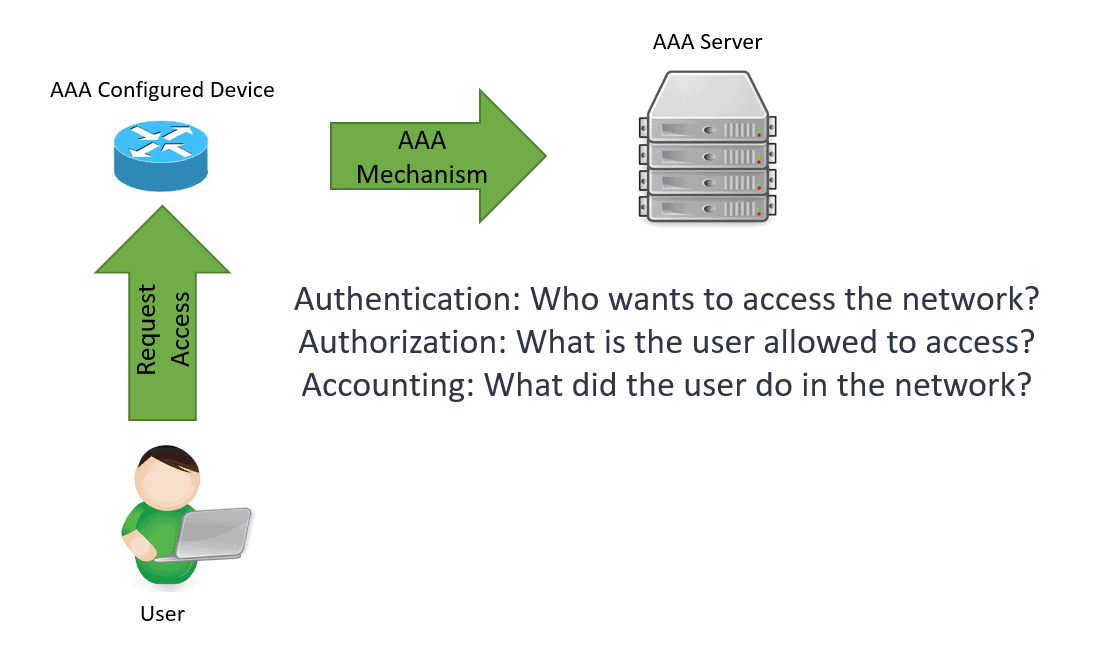
AAA, Authentication, Authorization, and Accounting framework manages the user’s activity on a network it wants to access by authentication, authorization, and accounting mechanism. AAA uses effective identity and access management that enhances network security by ensuring that only those granted access are allowed and their activities while in the network are monitored and logged.
AAA uses methods to challenge and handles user requests for network access by asking them for their authorized and authenticated user credentials to prove that they are legitimate users before gaining access to the network. AAA is widely used in network devices such as routers, switches, and firewalls, just to give a few to control and monitor access within the network.
AAA Server
AAA addresses the limitations of local security configuration and the scalability issues that come with it. For example, if you need to change or add a password, it has to be done locally and on all devices, which will require a lot of time and resources.
An external AAA server solves these issues by centralizing such tasks within the network. Having backup AAA servers in the network ensures redundancy and security throughout the network.
Authentication
The AAA server receives a user authentication request. It challenges the user’s credentials by asking for the username and password, for example, which is encrypted using a hashing algorithm. The AAA server compares the user’s authentication credentials with the user credentials stored in the database.
Authorization
Once the user’s credentials are authenticated, the authorization process determines what that specific user is allowed to do and access within the premise of the network. Users are categorized to know what type of operations they can perform, such as an Administrator or Guest. The user profiles are configured and controlled from the AAA server. This centralized approach eliminates the hassle of editing on a “per box” basis.
Accounting
The last process done in the AAA framework is accounting for everything the user is doing within the network. AAA servers monitor the resources being used during the network access. Accounting also logs the session statistics and auditing usage information, usually for authorization control, billing invoice, resource utilization, trend analysis, and planning the data capacity of the business operations.
AAA Protocols
There are two most commonly used protocols in implementing AAA, Authentication, Authorization, and Accounting in the network. RADIUS and TACACS+ are open standards that different vendors use to ensure security within the network.
Remote Authentication Dial-In User Service (RADIUS) Protocol operates on ports UDP 1645 and UDP 1812 that provide centralized AAA management for users who connect and use Network Access Server (NAS), such as a VPN concentrator, router, and switch. This client/server protocol and software enables remote access servers to communicate with a central server to perform AAA operations for remote users. This protocol operates at the application layer and can use TCP or UDP as a transport protocol.
Terminal Access Controller Access-Control System Plus (TACACS+) – is a remote authentication protocol that allows a remote access server to communicate with an authentication server to validate user access to the network. TACACS+ permits a client to accept a username and password and pass a query to a TACACS+ authentication server.
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training: