Security is compulsory in today’s generation because of emerging threats initiated by hackers ready to compromise your network and resources. There are three states of data that we need to protect – data at rest, data in use, and data in transit. Data in transit is more vulnerable to attacks as the data will travel outside your protected network. The best and cheapest option to protect our data in transit is by using Virtual Private Network (VPN). Cisco VPN solutions are offered as well.
Why Do We Need VPN?
A Virtual Private Network (VPN) is an encrypted tunnel between two or more devices, usually a firewall, such as the Cisco Adaptive Security Appliance (Cisco ASA), over an unsecured network such as the internet. All the network traffic that is sent through the VPN tunnel will be encrypted and kept confidential from hackers on a network or the internet. VPN replaces the dedicated point-to-point link with the emulated point-to-point link or secure connection that shares the common infrastructure.
Using VPN will cost you nothing as it is completely free since most organizations have firewalls already installed with a built-in VPN feature. VPN also provides security for all the traffic that is sent outside your network through VPN tunnels. Lastly, VPN is scalable in that you can add unlimited tunnels and users.
Two Types of VPN
There are two types of VPN that we are commonly using, and both are secured but implemented and used in different ways.
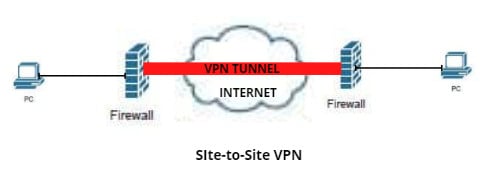
1. Site-to-Site VPN
Organizations are continuously expanding into different branches, and to protect the data in transit between two branches, we need to implement a site-to-site VPN. Common VPN protocols used in site-to-site VPN are Internet Security Protocol (IPSec). In implementing this type of VPN, we need to set up the Phase 1 and Phase 2 VPN negotiations. IKE Phase 1 negotiation is where we create a secure encrypted channel or encrypted network connectivity for the two firewalls can start the Phase 2 negotiation.
In IKE Phase 2 negotiation, the two firewalls will agree on the configured parameters that define what traffic can go via the VPN tunnel and how to authenticate and encrypt the traffic. The agreement is called Security Association. Both Phase 1 and Phase 2 should have the same parameters, such as pre-shared keys, authentication, encryption, and IKE version.
There are two ways to implement site-to-site VPN:
Intranet VPN – it provides secured site-to-site connectivity within the company or internally.
Extranet VPN – it provides secured site-to-site connectivity outside the company. For example, customers or partners can securely access the shared resources of the company.
The below image shows the Site-to-Site VPN implementation:
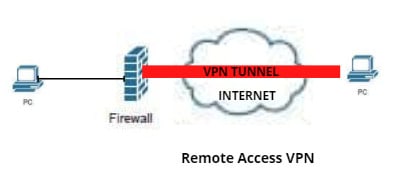
2. Remote Access VPN
Commonly called a mobile VPN. Using this type of VPN connection permits the users to connect through the internet anywhere in the world to access the corporate network resources securely. It can be used in a work-from-home setup where the employees can securely access the company’s internal resources through a VPN. To implement this, the employee must install a VPN client, such as a Cisco anyconnect secure mobility client or Cisco anyconnect VPN client, to their device, and a virtual IP address will be assigned to the employee’s device/PC that will be used to establish a secured tunnel.
Remote access VPN can use SSL, IKEv2, L2TP, and IPSec protocols. The most secure and easy to implement protocol is IKEv2. Some internet connections blocked the IKEv2 and L2TP protocols. That is why some are using SSL VPN as it uses the typical HTTP/HTTPS traffic that is allowed on all internet connection types. IPSec for remote access VPN is not usually used, as there is already a known vulnerability on the protocol.
The system administrator can choose between two modes to implement the remote access VPN:
Full Tunnel – all the traffic that is coming out from the employee’s device will go directly to the firewall, and the firewall will forward it to the internet if necessary. This is a completely secured implementation as all the security services of the firewall will be applied to all the traffic coming out from the employee’s device.
Split Tunnel – the traffic that will go to the internet like HTTP/HTTPS traffic will go to the typical internet connection such as broadband/LTE, while the VPN traffic will be used to access the internal resource of the company will use a VPN tunnel. The traffic will be split based on its purpose.
The below image shows the Remote Access VPN implementation:
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training: