Before tackling symmetric vs. asymmetric encryption and its key differences, let us first see what cryptography is. Cryptography transforms readable messages into an unintelligible (impossible to understand) form and later reverses the process. It can send sensitive data securely over an untrusted network that uses authentication and encryption methods such as Symmetric and Asymmetric encryption.
Cryptography Services
Cryptography provides the following services to the data:
- Authenticity (Proof of source)
- Confidentiality (Privacy and secrecy)
- Integrity (the data has not changed during transit)
- Non-Repudiation (Non-deniability)
Symmetric Encryption
Symmetric encryption is a type of encryption that uses public key encryption. The same secret key that both encrypts and decrypts data and is known by both parties. The public key cryptography method is faster, and it is typically used in encrypted data with large transmission such as email, secure web traffic, IPsec. Symmetric encryption algorithms include DES, 3DES, AES, and SEAL.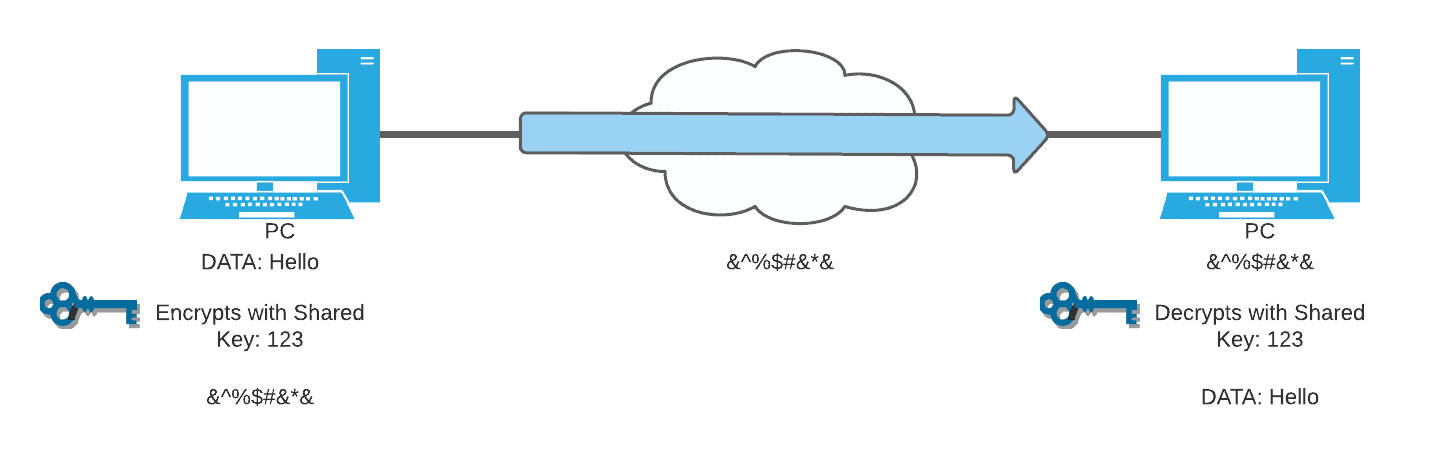
Take a look at the symmetric encryption process above. The same key is used to encrypt data, and the duplicate public keys are used to decrypt data. First, the sender specifies the data, then proceeds in encrypting data to unreadable format, forwards it to the transit. When the receiver receives that data, it is still encrypted, decrypt data using the same key, and then it is read. Notice that the data during the transit is jumbled so that if somebody tries to sniff it, they would not understand the data because they need that one key to decrypt it.
Asymmetric Encryption
Asymmetric encryption uses a secret key/private key and public key pairs. The message is encrypted with the public key and can only be decrypted with the secret key and vice versa. With asymmetric encryption, only the private key must be kept secret, and the public key can be ready in the public domain. Asymmetric Encryption is slower than symmetric encryption, and it is used for smaller transmissions like Symmetric Key Exchange and Digital Signatures. Asymmetric encryption algorithms include RSA and ECDSA.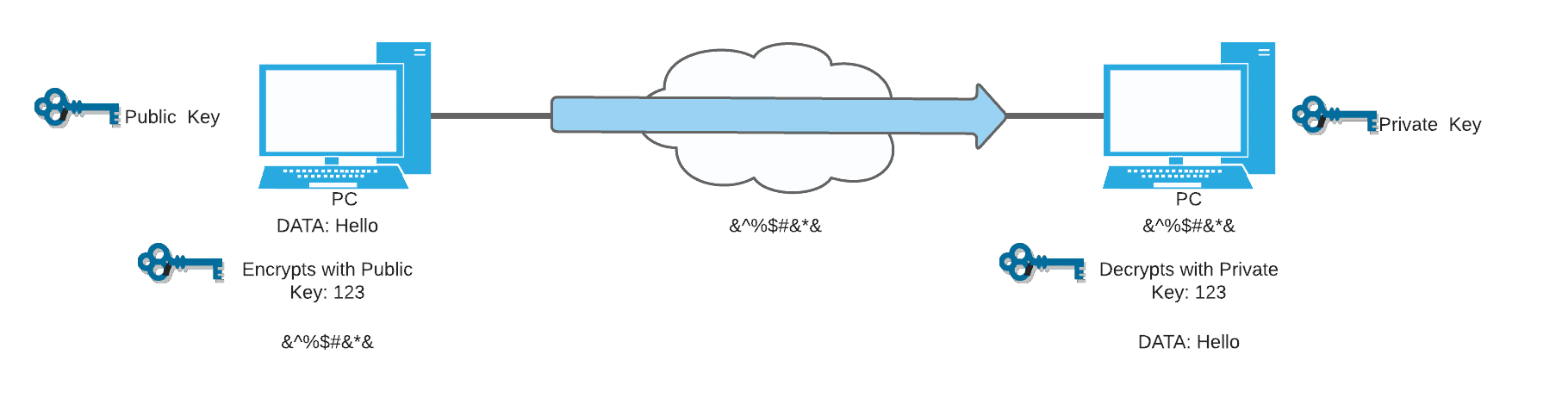
In the asymmetric encryption process above, you see that from the left, the sender has the public key, while the receiver on the right has the private key. Those are the keys they use for the encryption and to make the data jumbled when it passes to the transit network. Lastly, the data will be decrypted with the private key on the receiving end. This enables everyone to send data securely to the host with a private key, and it is exclusive for those who have the private key, so only those who can decrypt the message.
Authenticity and Non-Repudiation
As you can see on the image below, if the host with the secret key or private key sends data to the server with the public key, it is apparent that the sender would be that particular sender because it has been authenticated. Therefore, there is no point in denying or repudiating it. The encrypted message contains decrypted information that was acquired during the decryption process.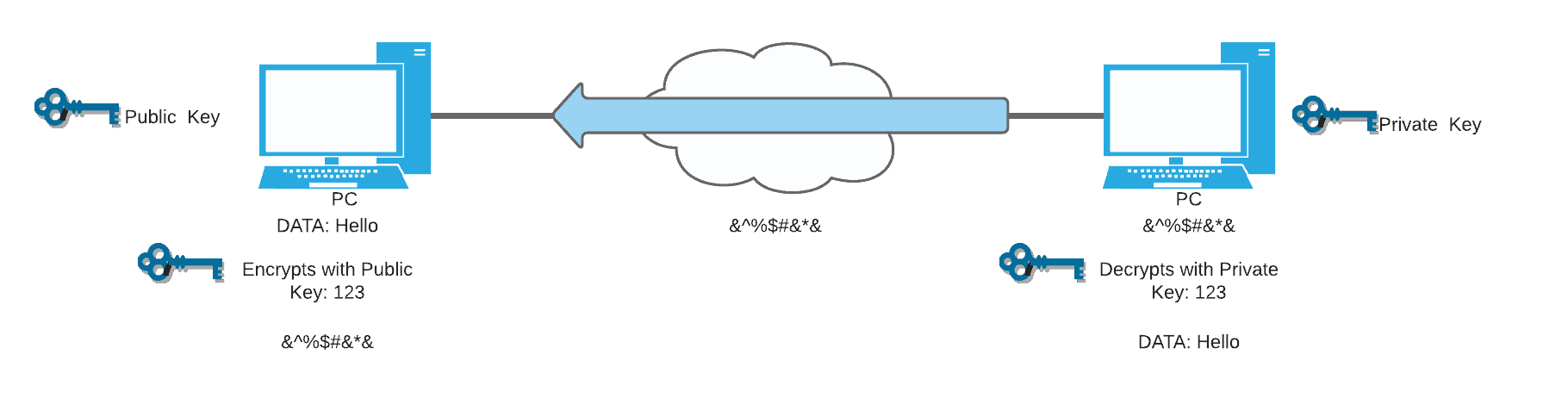
Hash-Based Message Authentication Codes (HMAC)
HMAC codes provide data security and integrity. The sender makes a hash value from the data to be sent using a symmetric key. If the hash values do not change, it is an indication the data has not been altered in transit. HMAC is usually used for large transmissions such as email, secure web traffic, and IPsec. HMAC algorithms include MD5 and SHA.
Public Key Infrastructure (PKI)
Cryptography can be used to send sensitive data securely over an untrusted network. Symmetric key encryption is used for bulk data transmissions. Therefore, each side needs to know the shared key, which leads to a problem.
For example, when you want to buy something online, you want your credit card details to be encrypted over the internet. The online store cannot send you the shared key over the same Internet channel because your connection is not yet encrypted. Anybody that sniffs your data in real-time will get the shared key as well if it is sent on the same line. It is not even practical to call a customer every time someone wants to purchase just to give them the shared key. So, how do we resolve this?
Public Key Infrastructure (PKI) solves this problem. It uses a trusted introducer, Certificate Authority, for the two parties who need secure communication, digital certificates. Also, both parties need to trust the Certificate Authority.
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
