There are two Access Control List (ACL) types:
1. Standard Access Control Lists – with standard access lists, you can filter traffic only on the source IP address of a packet. These types of access lists are not as powerful as extended access lists, but they are less processor-intensive for the router.
The following example describes the way in which standard access lists can be used for traffic flow control:
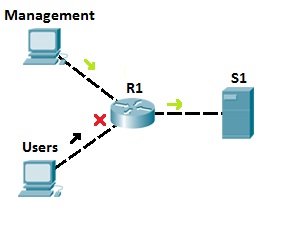
Let’s say that server S1 holds some important documents that need to be available only to the company’s management. We could configure an access list on R1 to enable network access to S1 for the users from the management network only. All other traffic going to S1 will be blocked. This way, we can ensure only authorized users can access sensitive files on S1.
2. Extended Access Control Lists – with extended access lists, you can be more precise in your network traffic filtering. You can evaluate the source and destination IP addresses, type of layer 3 protocol, source and destination port, etc. Extended access lists are more complex to configure and consume more CPU time than standard access lists, but they allow a much more granular level of control.
To demonstrate the usefulness of extended ACLs, we will use the following example:
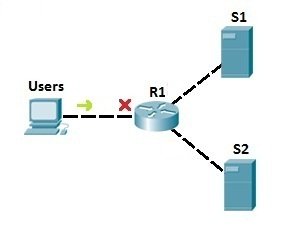
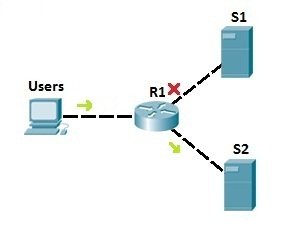
In the example network above, we have used the standard access list to prevent all users from accessing server S1. But, with that configuration, we also deny access to S2! To be more specific, we can use extended access lists. Let’s say that we need to prevent users from accessing server S1. We could place an extended access list on R1 to prevent users only from accessing S1 (we would use an access list to filter the IP traffic according to the destination IP address). That way, no other traffic is forbidden, and users can still access the other server, S2:
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training: